Sharing a private message containing sensitive information has become one of the most common yet risky activities in our digital lives. Whether you need to send a temporary password, share confidential login credentials, or transmit secret data to a colleague, traditional communication channels like email or chat apps leave permanent traces that can be intercepted, leaked, or discovered months later. This creates a genuine security problem for individuals and businesses alike. The solution lies in self-destructing messages - a free online tool approach that ensures your sensitive information vanishes after being read, leaving no digital footprint behind.
Content Table
Why Traditional Messaging Fails for Sensitive Data
Every day, millions of people share secret messages through email, Slack, WhatsApp, or SMS without realizing the risks. These platforms store your messages indefinitely on multiple servers. Your "private" conversation exists in at least three locations: your device, the recipient's device, and the service provider's servers.
Consider these real constraints that make traditional messaging dangerous for sensitive data:
- Permanent storage: Emails containing secret login credentials remain searchable in inboxes for years
- Multiple access points: IT administrators, hackers, and even former employees may access archived messages
- Legal discovery: Stored messages can be subpoenaed in legal proceedings
- Account compromises: If someone gains access to an email account, they see the entire history
The fundamental problem is simple: once you send a traditional message, you lose all control over it. You cannot guarantee deletion, and you have no way to verify that the information was destroyed after use. This is where self-destructing private message tools provide a critical advantage. Learn more about how to keep your private messages truly secure.
How Self-Destructing Private Messages Work
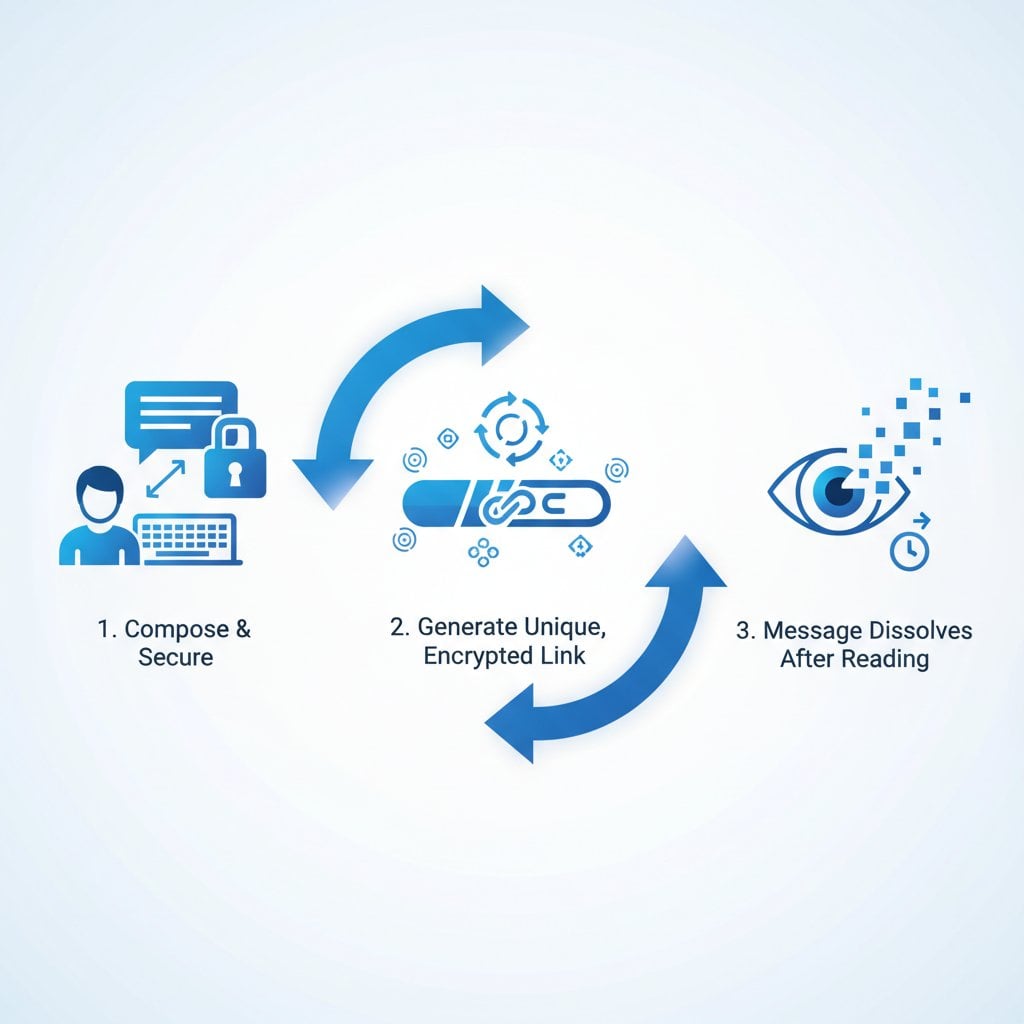
Self-destructing message services operate on a fundamentally different principle than traditional messaging. Instead of storing your message permanently, these tools create a unique, one-time link that automatically destroys the content after it has been viewed.
The technical process involves several security layers:
- Client-side encryption: Your message is encrypted in your browser before transmission
- Unique link generation: The system creates a one-time URL containing the decryption key
- Secure storage: The encrypted message is stored temporarily on the server
- Single-view access: When the recipient opens the link, they see the message once
- Automatic destruction: The message is permanently deleted after viewing
This approach addresses the core problem of secret data transmission. Even if someone intercepts the link after it has been used, they find nothing - the message no longer exists. For a deeper understanding of the cryptographic methods involved, read our Advanced Encryption Guide covering AES, RSA, ECC and Post-Quantum Cryptography.

Technical Note: Modern self-destructing message tools use AES-256 encryption, the same standard used by governments and financial institutions worldwide. This ensures that even if data were somehow intercepted during transmission, it would be practically impossible to decrypt without the unique key.
Step-by-Step Guide to Sending Secure Messages
Using a free online tool to send self-destructing messages requires no technical expertise. Follow these actionable steps to share your secret messages safely:
Step 1: Prepare Your Sensitive Information
Before creating your private message, organize the information you need to share. This might include:
- Temporary passwords or API keys
- Secret login credentials for shared accounts
- Confidential business data or financial information
- Personal identification numbers or security codes
Step 2: Access the Secure Message Tool
Navigate to our secure messaging platform. No account registration is required, which means no personal data is collected or stored about you.
Step 3: Compose and Encrypt Your Message
Type or paste your sensitive content into the message field. The encryption happens automatically in your browser. Consider these practical tips:
- Include only the essential information needed
- Add context so the recipient understands the purpose
- Specify any time-sensitive requirements
Step 4: Configure Security Options
Select additional security settings based on your needs:
- Expiration time: Set a deadline after which the unread message self-destructs
- Password protection: Add an extra layer with a separate password
- View notification: Receive confirmation when the message is opened
Step 5: Generate and Share the Link
Click generate to create your unique, one-time link. Copy this link and share it with your recipient through your preferred channel. The link itself contains no readable information about the message content.
Step 6: Confirm Destruction
After the recipient views the message, the content is permanently deleted. If you enabled notifications, you will receive confirmation that the message was successfully delivered and destroyed.
For more details on this process, see our guide on anonymous self-destructing messages and sending safe messages.
Real-World Use Cases
Understanding practical applications helps you identify when self-destructing private messages provide the most value. Here are the most common scenarios where this approach solves real problems:
Use Case 1: IT Credential Sharing
System administrators frequently need to share secret login credentials with new employees or contractors. Instead of emailing passwords (which remain in both sent and received folders indefinitely), a self-destructing message ensures the credentials exist only long enough for the recipient to use them.
Practical constraint: The recipient must save the credentials locally before the message disappears. Include instructions reminding them to do so.
Use Case 2: Financial Information Transfer
Accountants, lawyers, and financial advisors often need to transmit sensitive client data. Bank account numbers, tax identification numbers, and investment details require secure transmission. Self-destructing messages provide an audit-free method that leaves no digital trail.
Use Case 3: Healthcare Communications
Medical professionals sharing patient information must comply with strict privacy regulations. While this does not replace HIPAA-compliant systems for official records, self-destructing messages work well for quick, necessary communications that should not be permanently stored.
Use Case 4: Personal Privacy Protection
Individuals sharing WiFi passwords, security codes, or personal account access with family members benefit from messages that automatically disappear. This prevents the information from being discovered if devices are lost, stolen, or accessed by others.
Learn more about how one-time links prevent data leaks in our article on what are one-time secret links.
Key Takeaways:
- Traditional messaging stores sensitive data permanently across multiple servers, creating ongoing security risks
- Self-destructing messages use client-side encryption and automatic deletion to eliminate digital traces
- No registration required means no personal data is collected about you or your communications
- Practical applications range from IT credential sharing to financial data transfer and personal privacy
Hypothetical Case Study: Marketing Agency Credential Sharing
Note: This is a hypothetical example created to illustrate practical application. It does not represent a real company or actual events.
The Situation
Imagine a digital marketing agency called "BrightPath Marketing" with 25 employees managing social media accounts, advertising platforms, and analytics tools for 40 different clients. Each client relationship involves multiple secret login credentials: social media accounts, Google Analytics access, advertising platform logins, and content management systems.
The Problem
Previously, the agency shared credentials through a combination of email, Slack messages, and shared spreadsheets. This created several problems:
- Former employees retained access to old emails containing client credentials
- A compromised employee email account exposed dozens of client logins
- No way to verify whether shared credentials were still accessible in old messages
- Clients expressed concern about their secret data being stored in multiple locations
The Solution
BrightPath implemented a policy requiring all credential sharing to use self-destructing private messages. The process worked as follows:
- When onboarding a new client, the account manager creates a self-destructing message containing initial credentials
- The unique link is shared via the agency's project management system
- The team member accessing the credentials saves them to the agency's password manager
- The original message automatically deletes after viewing
The Results
After implementing this approach, the hypothetical agency would experience:
- Zero instances of credentials remaining in email archives
- Simplified offboarding process (no need to search old messages for shared credentials)
- Increased client confidence in data handling practices
- Reduced risk exposure from potential email account compromises
Best Practices for Maximum Security
While self-destructing messages provide strong protection, following these best practices maximizes your security:
Separate the Link and Context
Never send the self-destructing link and explanation of what it contains through the same channel. For example, send the link via email but notify the recipient via text message that they should check their email for important credentials.
Use Password Protection for Critical Data
For highly sensitive secret data, enable password protection on your message. Share the password through a different communication channel than the link itself. This two-factor approach ensures that intercepting either piece alone provides no access.
Set Appropriate Expiration Times
Configure your message to expire within a reasonable timeframe. A message containing a temporary password probably does not need to remain available for a week. Shorter expiration windows reduce the risk of unauthorized access.
Verify Recipient Identity
Before sharing secret login credentials, confirm you are communicating with the intended recipient. A quick phone call or video chat verification prevents social engineering attacks where someone impersonates a colleague.
For comprehensive security guidance, explore our privacy best practices for digital communication.
Conclusion
Protecting sensitive information in digital communications requires more than good intentions. It demands tools designed specifically for security. Self-destructing private messages solve the fundamental problem of permanent data storage by ensuring your secret messages, login credentials, and confidential data exist only as long as necessary.
The combination of client-side encryption, one-time links, and automatic deletion creates a communication method that leaves no traces for hackers, unauthorized employees, or legal discovery to find. Whether you are sharing secret login details with a colleague or transmitting sensitive business information to a client, self-destructing messages provide the security traditional channels cannot match.
Ready to share your sensitive information safely? Try our free secure messaging tool and experience the peace of mind that comes with truly private communication.